
Decipher the rise of cybersecurity problems in 2024. (Source – Shutterstock).
- Cybersecurity challenges in 2024 will intensify with AI and phishing threats at the forefront, requiring stronger defenses.
- THE Law of no confidence targets non-consensual AI-generated images, reflecting urgent cybersecurity law updates.
- Incidents like Lush highlight the need for improved cybersecurity and legislative response in 2024.
As we enter 2024, the digital landscape is witnessing an unprecedented surge in cyberthreats, marked by significant breaches as early as February. The resumption of activities by Russian piratestargeting key technology companies, including a notable intrusion at Hewlett Packard Enterprise (HPE) linked to a group known for compromising Microsoft email accounts, highlights the seriousness of the situation.
Similarly, Malaysia is facing an increase in data security breaches, highlighting the urgent need for more robust cybersecurity measures. The urgency of this issue has catalyzed efforts by government and business sectors to better improve cybersecurity laws and practices to counter these emerging threats.
A recent Keeper Security study, which surveyed more than 800 IT security leaders worldwide, reveals a worrying trend: 95% of respondents say cyberattacks have reached unprecedented levels of sophistication. The study highlights AI-based attacks and phishing as the most serious and rapidly growing threats.
Cybersecurity Challenges Evolve in the Age of AI and Deepfakes
The cybersecurity environment of 2024 is complex and evolving, with AI and deepfake technologies identified as significant new threats. This evolution requires reassessing security strategies to effectively address current and future challenges.
The survey identified the top five attack vectors: AI-based attacks, deepfake technology, supply chain attacks, cloud jacking and Internet of Things (IoT) attacks. highlighting the diverse nature of the threats organizations currently face.
A significant incident involving the misuse of AI and deepfake technology targeted Taylor Swift, prompting legislative action in the United States. A bipartisan group of senators introduced the Law of no confidence to criminalize the distribution of non-consensual and sexualized AI-generated images, in response to the widespread distribution of such content involving Swift on social media platform X.
THE Law of no confidence aims to allow victims of digital counterfeiting to bring civil claims against those who create, possess or distribute these images without consent. The initiative, led by Senators Dick Durbin, Lindsey Graham, Amy Klobuchar and Josh Hawley, addresses growing concerns about AI-generated sexual content.
The spread of fake sexually explicit images of Swift highlighted the ease of creating and sharing deepfakes, raising significant concerns about digital consent and privacy. Although artificial, the damage caused by these images is real, leading Swift’s fans and social media platforms to limit their distribution. X, in particular, has taken steps to restrict Swift-related searches to curb the spread of these harmful images.
Singapore faces similar challenges with deep counterfeiting technology, where personalities, including the Prime Minister, were misrepresented in fraudulent content. These incidents have sparked discussions about the need for increased vigilance and stricter measures against the misuse of digital identities for fraudulent promotions.
Global IT leaders have identified the fastest growing attack vectors as phishing, malware, ransomware, password attacks and denial of service (DoS).
The case of Akira’s violation of Lush
In a notable cybersecurity incident, British company Lush, known for its cosmetics and bath products, was the victim of a cyberattack claimed by the Akira ransomware group. Lush hired computer forensics experts to investigate the breach, initially reported on January 15, 2024. Chester Wisniewski of Sophos highlighted the incident as a ransomware or extortion attack by Akira, who publicly claimed responsibility for the theft 110 GB of data.
Akira’s acknowledgment of the attack on Lush and the ambiguity over the nature of the attack (whether it was ransomware, extortion, or both) demonstrate the group’s flexibility in its criminal activities. The lack of notable disruption to Lush’s operations could indicate that encryption was not part of the attack.
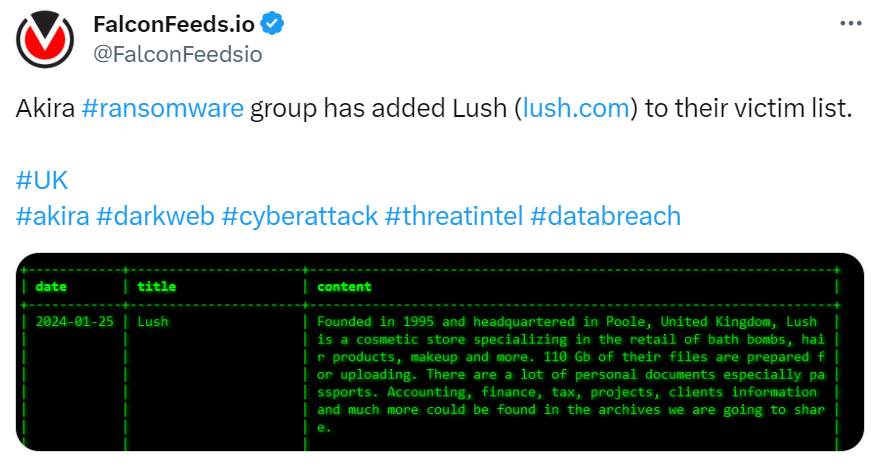
The Akira ransomware group has added Lush to its list of victims. (Source – X).
Wisniewski has observed Akira’s growing prominence in cybercrime, exploiting vulnerabilities including in Cisco VPN products and remote access tools without multi-factor authentication (MFA).
The breach at Lush highlights the importance of quickly updating all external network components and implementing MFA for remote access, underscoring the importance of basic cybersecurity practices.
The importance of being cyber aware
Additionally, Darren Guccione, CEO and co-founder of Keeper Security, highlights the paradox presented by emerging technologies like AI, which, while offering advancements, also pose significant cybersecurity risks if not managed appropriately.
Guccione emphasizes that with today’s cybersecurity tools, we can address these emerging challenges, turning potential vulnerabilities into opportunities to strengthen our digital defenses.
As the threat landscape evolves, IT leaders must adapt to protect against these emerging threats. Implementing solutions such as password managers and privileged access management systems is crucial. These tools enforce strong password protocols and manage access to critical assets, forming a comprehensive security strategy that limits unauthorized access and improves the resilience of cybersecurity infrastructures.


