Modern cybersecurity is a game of speed. With attacks now occurring in minutes, the agility with which security teams can detect and disrupt adversaries can mean the difference between being the hunter and the prey.
However, it can be difficult for security teams to regain the speed advantage over their adversaries. Today’s defenders face unstaffed security positions, crippling complexity, and a relentless volume of alerts, which exacerbate response times and force teams to waste minutes on non-urgent tasks. Meanwhile, adversaries are reaching new heights of sophistication and stealth, increasingly powered by AI and automated technologies.
To help teams stop breaches faster and more effectively than ever before, CrowdStrike is announcing four breakthrough AI innovations to improve and accelerate every step of the analyst experience. These additions will enable seamless data ingestion, reimagine alert prioritization, visualize potential attack paths, and accelerate detection triage. Each innovation leverages AI to break down persistent barriers to effective threat response, including manual data integration, frantic and unprioritized alerts, overlooked blind spots, and error-prone decision-making during incident triage.
Frictionless data ingestion with industry-first AI-powered parsers
One of the biggest challenges security teams face occurs before they even begin analyzing detections, starting with data integration. Security teams are overwhelmed with data from countless new sources, each with its own unique log format. Developing custom parsers for these logs can be a time-consuming and resource-intensive process, especially since formats are constantly evolving. Keeping up with these changes while ensuring data remains accurate and accessible is a constant struggle, often leading to deployment delays, increased costs, and team overload.
CrowdStrike Falcon® Next Generation SIEM is changing the game with AI-generated analyzers, which enable SOC teams to quickly ingest and process data from any source. Instead of painstakingly writing analyzers and manually updating them every time the log format changes, teams can harness the power of generative AI to instantly create analyzers based on representative logs.
To generate analyzers, users simply provide sample log records. From there, Falcon Next-Gen SIEM analyzes the samples with multiple large language models (LLMs) to learn their structure and log content. AI-generated analyzers adhere to the CrowdStrike analysis standard, ensuring seamless correlation and improved threat detection.
By dynamically creating analyzers, security teams can eliminate hours of tedious work and accelerate Falcon Next-Gen SIEM deployment. Discover the latest innovations that facilitate data integration for effortless replacement of legacy SIEMs.
Proactive exposure management through AI-based attack path analysis
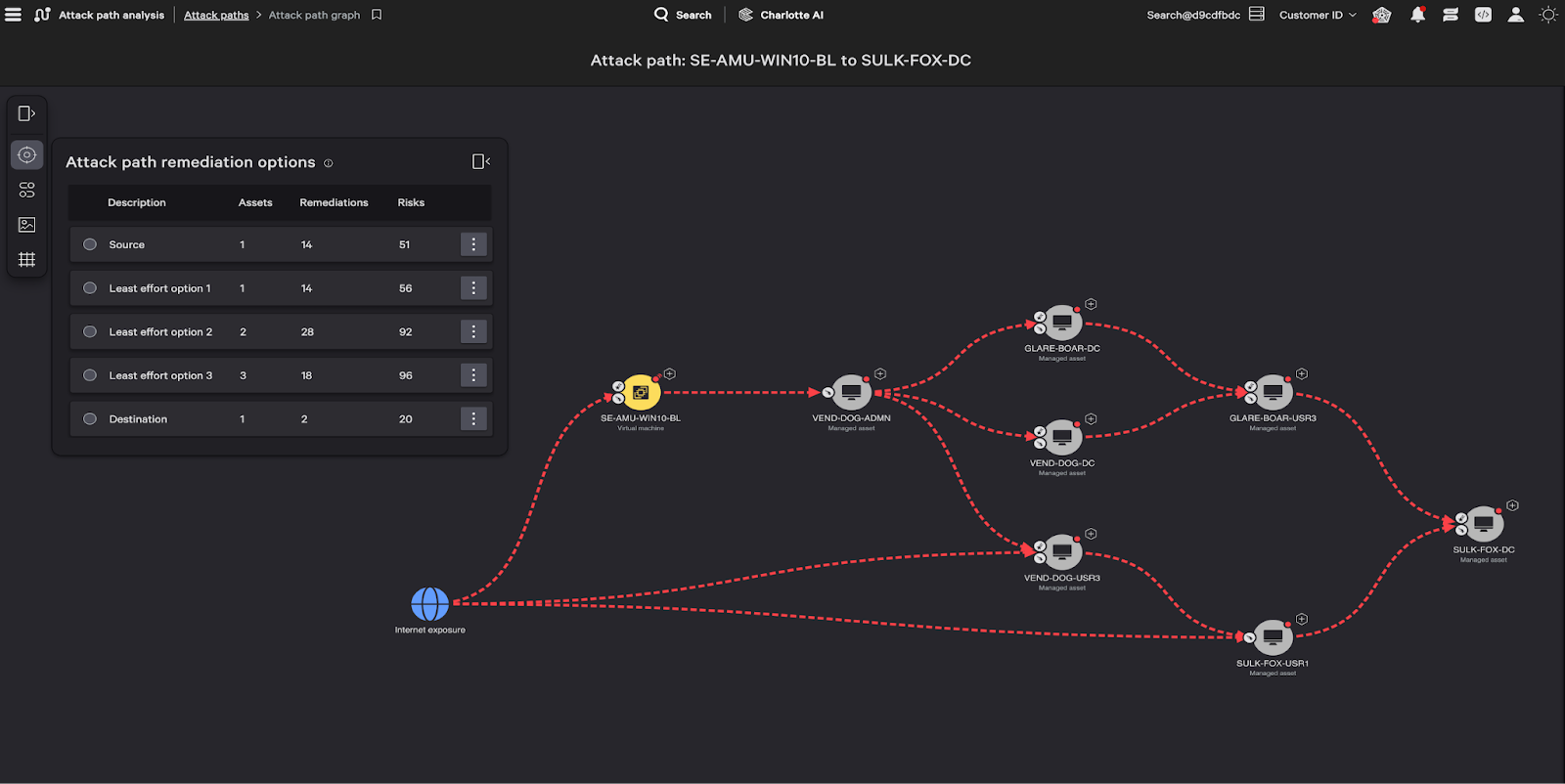
Another recurring challenge security teams face is proactive risk management. With thousands of vulnerabilities and limited resources, prioritization is a difficult but critical task for security teams. Traditional vulnerability management tools often prioritize vulnerabilities based on individual severity scores, which don’t provide enough context to effectively prioritize: More than 50% of all CVEs Vulnerabilities are classified as high or critical severity based on CVSS scores, providing limited information to work with. These scores also ignore the environmental context of the organization’s asset landscape, which informs exploitability.
Delivered by CrowdStrike Falcon® Exposure ManagementCrowdStrike’s Attack Path Analysis (APA) addresses these challenges with predictive AI and machine learning technology. It improves vulnerability severity assessment with ExPRT.AI, CrowdStrike’s proprietary technology trained on real-time threat intelligence and billions of daily detection events. ExPRT.AI predictively and dynamically assesses the exploitability of a vulnerability to reduce the percentage of true critical issues teams need to focus on. Machine learning algorithms help detect asset roles to inform the business criticality of an asset, whether it’s a jump host, mail server, or web server, providing important environmental context.
Armed with this information and deep insights from the CrowdStrike Falcon® platform, APA maps how attackers could enter and move laterally within the customer’s environment to compromise critical systems. It distinguishes actual attack paths from theoretical ones and identifies chokepoints or dead ends so teams can strengthen their defenses to proactively block the paths.
Additionally, CloudStrike APA is able to map the interconnections between cloud and on-premises assets, adapting to the reality of the hybrid infrastructure most customers live in, and highlighting attack predictors based on traditional CVEs and cloud-native misconfigurations. It also provides prioritized, high-impact, low-effort remediation recommendations so teams can act quickly, facilitating a targeted response, especially in zero-days where every minute counts. As the saying goes, attackers think in graphs, defenders think in lists. With APA, defenders can now visualize the attacker’s perspective to get ahead of the game.
Automated Leads Powered by CrowdStrike Signal
Another prioritization challenge arises when security teams need to find the “needle in the haystack” and identify detections that deserve analyst attention. Traditional detection systems often struggle to identify complex threats and can overwhelm analysts with numerous non-priority alerts. These traditional approaches often apply generic rules and thresholds that don’t account for the unique characteristics of each environment. Without the help of AI, analysts must manually sort through and collate disparate information, leading to alert fatigue and the risk of missing threats.
CrowdStrike Signal, a new AI-powered engine for CrowdStrike Falcon® Insight XDRaddresses these challenges by intelligently generating and prioritizing automated leads. By aggregating related events into actionable insights and providing a clear starting point for investigations, CrowdStrike Signal reduces noise, accelerates detection and response, and ensures security analysts of all skill levels can quickly identify and neutralize threats.
CrowdStrike Signal improves early threat detection by analyzing a wide range of data, including subtle and early indicators, enabling security teams to identify and respond to potential threats before they can cause harm. With Signal’s AI-driven approach, detection adapts to the specific characteristics of each environment. This ensures that only the most relevant and critical threats are detected for human validation, enabling more accurate prioritization and response. By adapting to your organization and providing a quick measure of its current posture, Signal reduces the likelihood of missing threats and improves overall security.
Accelerated response with GenAI-driven detection triage
The final challenge security teams face is accelerating triage and response capabilities. To further reduce investigation and response times (MTTR), security teams will be able to invoke CrowdStrike® Charlotte AI™ to accelerate detection triage, expediting the most time-consuming and error-prone components of initial triage: distinguishing between true and false positives and reporting their assessments. This feature will allow Charlotte AI users to apply world-class detection triage guidance from CrowdStrike experts to incoming detections with the speed, consistency, and scale of AI. As with all actions enabled by Charlotte AI, users will be able to pre-configure the classes of detections to which this feature can be applied and use CrowdStrike Falcon® Fusion SOAR to decide what actions can occur based on the AI findings.
When a new detection is raised, Charlotte AI will first analyze it to determine if it is a true or false positive and provide an associated confidence level for its assessment. Charlotte AI will also recommend whether the detection should be closed or escalated to a human analyst. During this triage phase, analysts will be able to make Charlotte AI’s escalation decisions a condition in Falcon Fusion’s SOAR workflows to automatically notify analysts when to begin a forensic analysis or investigation. Finally, Charlotte AI will generate an explanation summarizing its findings and recommendations (see figures below).
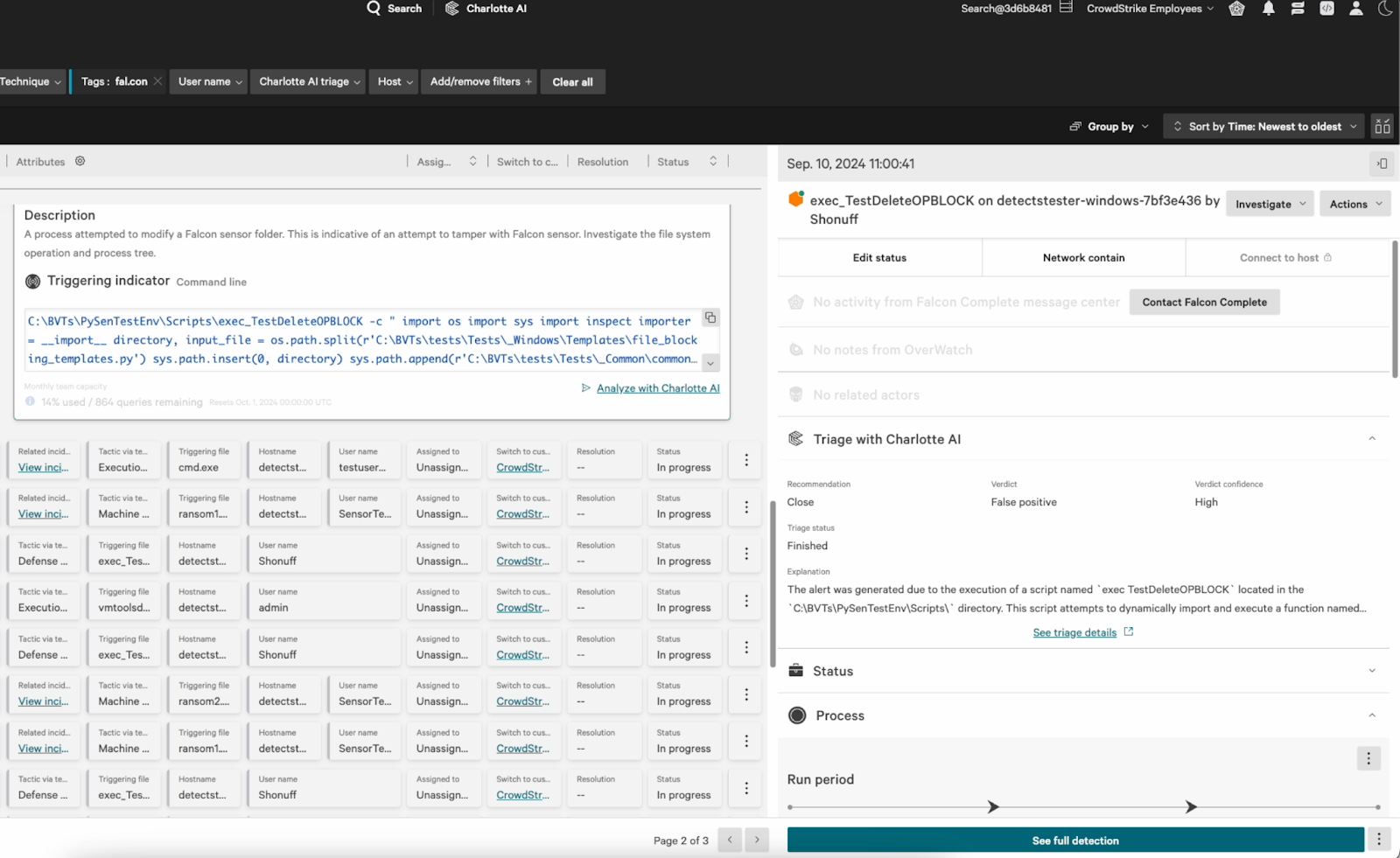
Figure 2. Charlotte AI determines that a detection is likely a false positive (non-malicious), recommends closing the detection, and explains its recommendation. (Click to enlarge)
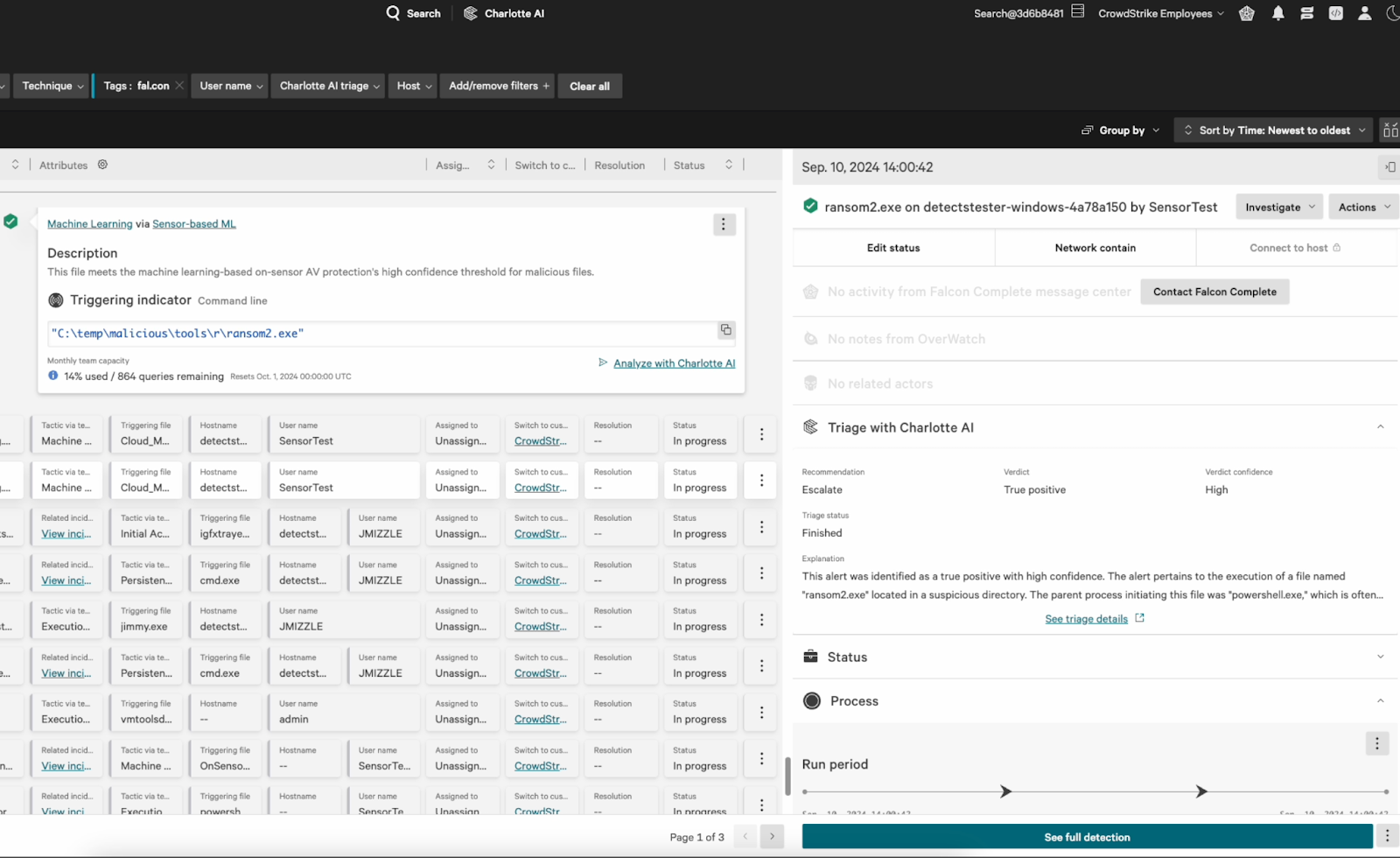
Figure 3. Charlotte AI determines that a detection is likely a true positive and recommends forwarding it to an analyst for further investigation. (Click to enlarge)
Next steps
- Learn more about what’s new on Falcon.
- Check out the latest from Fal.Con, including keynotes and live streams sessions.
- Here Falcon 2024? Learn more about the AI Sessions what excites us the most.